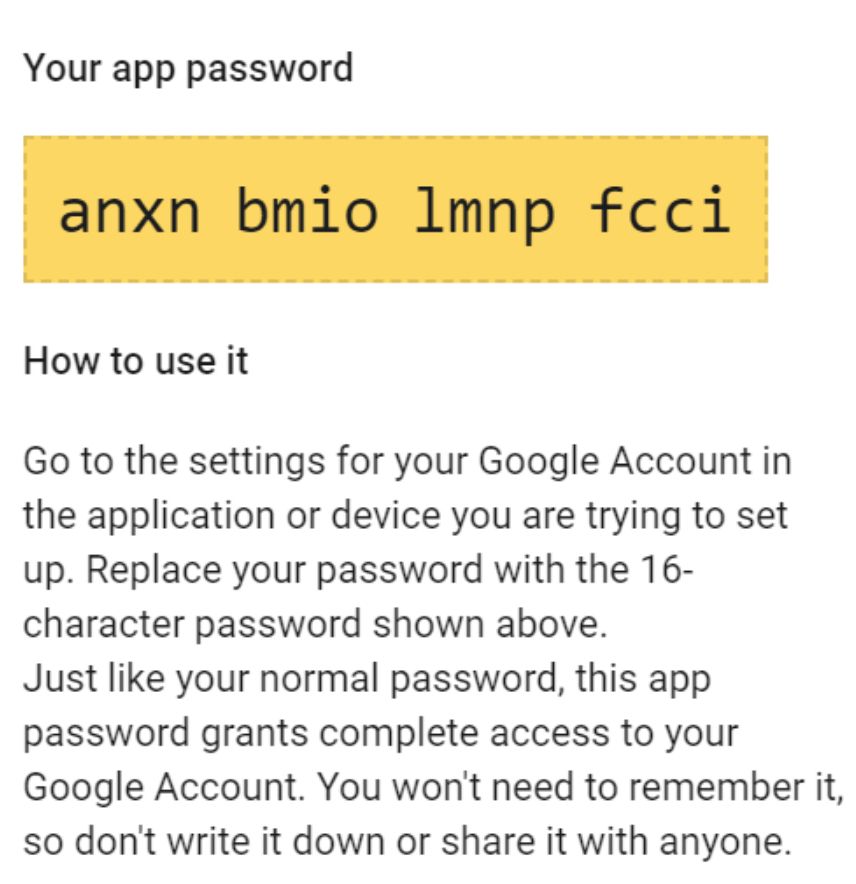
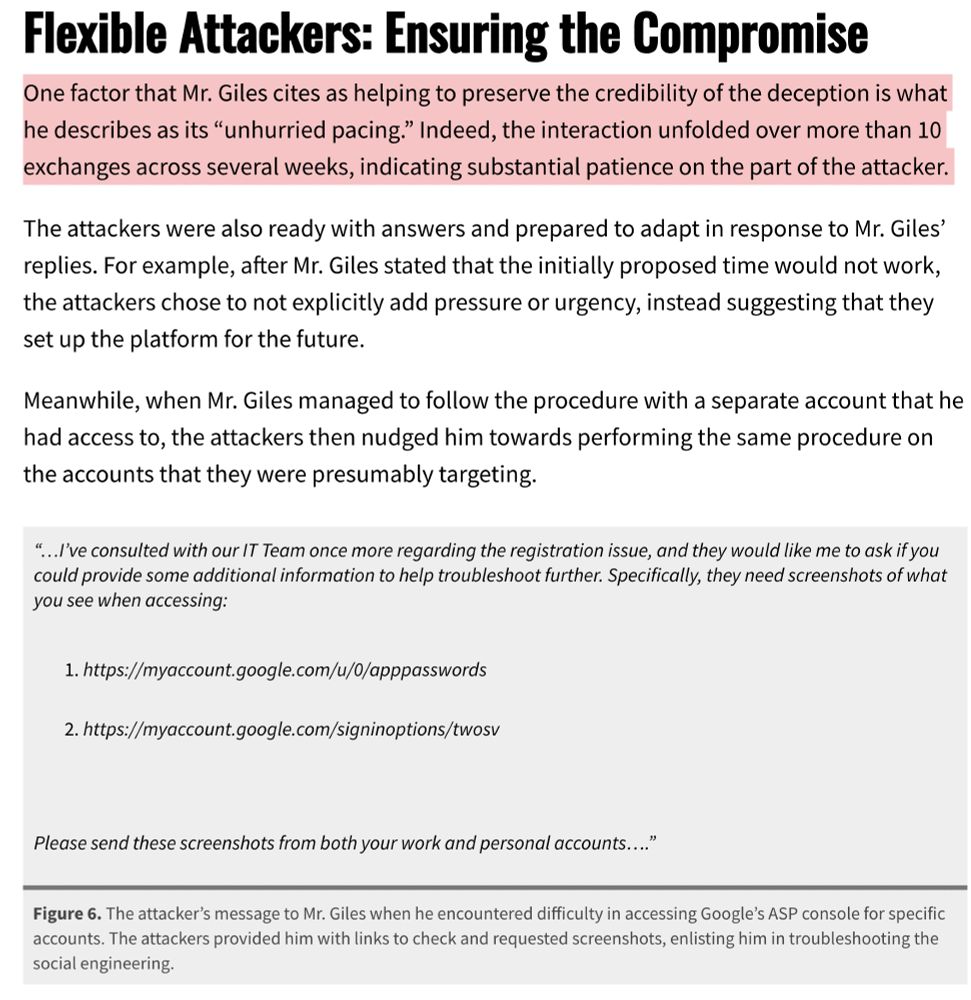
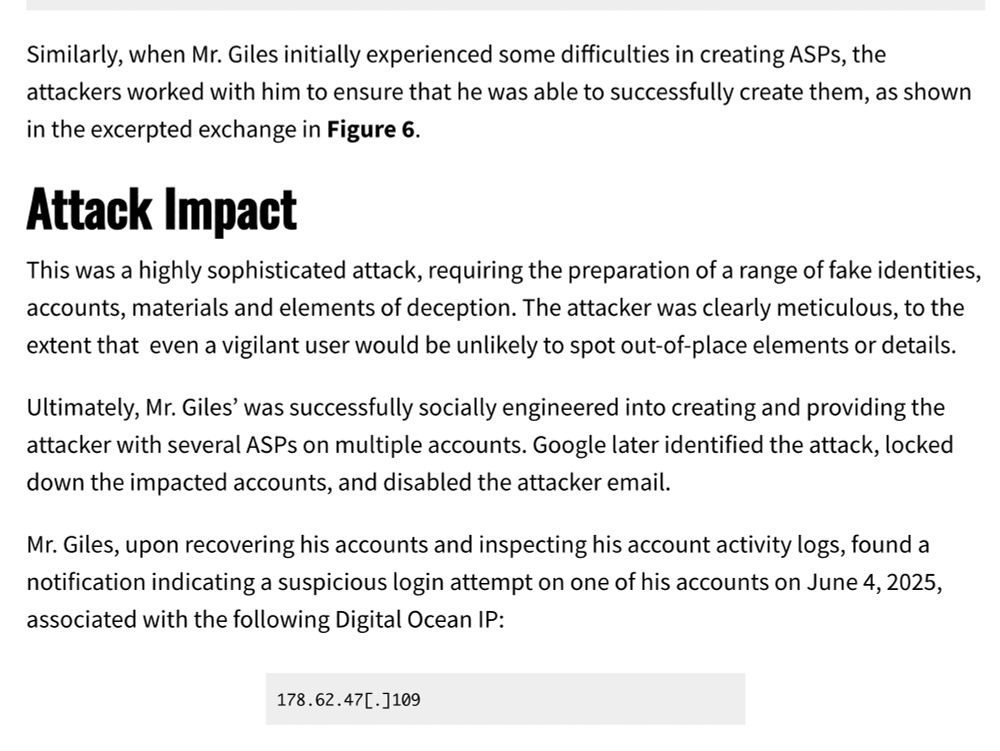
7/ This attack was like slow food. 10 email exchanges over several weeks! No overt pressure! Very much not your run-of-the-mill phishing. Ultimately, @keirgiles.bsky.social realized something was wrong and got in touch with us @citizenlab.ca...but not before the attackers got some of his ASPs...
Replies
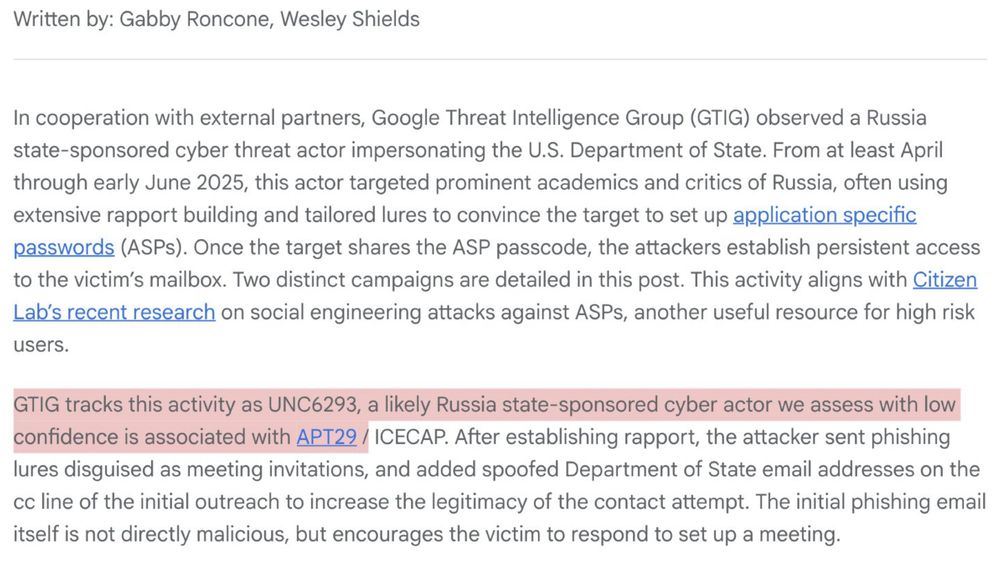
8/ Who targeted @keirgiles.bsky.social ? Enter the Google Threat Intelligence Group w/analysis & attribution! Great! Our bad actors are: 🇷🇺 #UNC6293, a #Russian state-sponsored threat actor. Google adds bonus additional low confidence association to #APT29 (that would be the #SVR). Nice people.
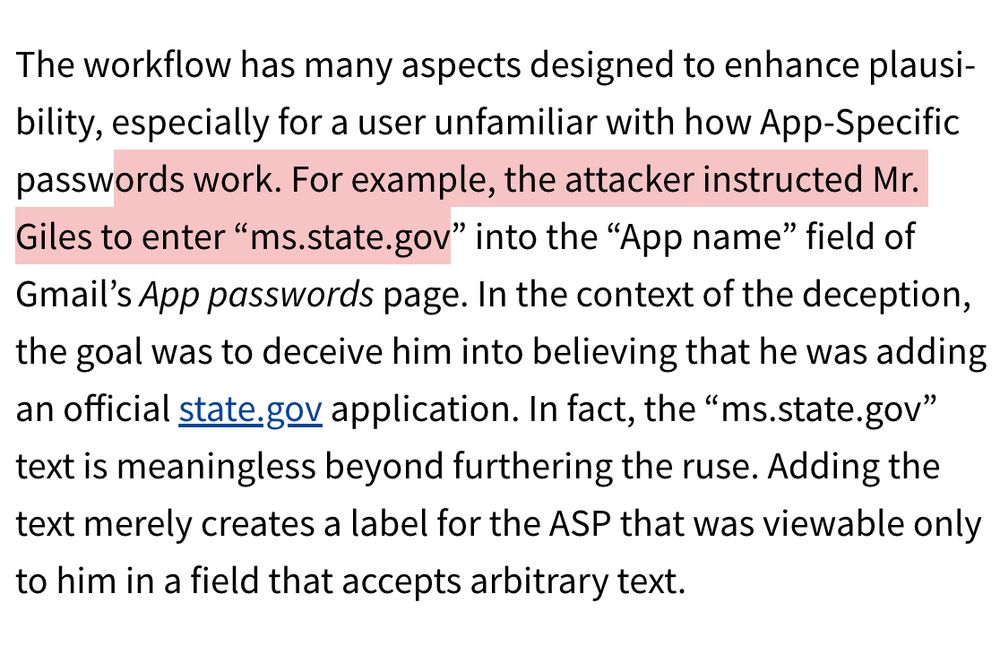
9/ There were so many clever bits to this attack, it's easy to imagine a lot of people falling for it. Everything was clean. Foc looked real. The language was right. Email addresses at the State Dept. seemed to be CC'd.. I could go on. They even had Keir enter "ms.state. gov" into the ASP name...
10/ Takeaway: some gov-backed groups are feeling pressure & experimenting. Moving from smash & grab phishing... to subtler, slower & perhaps less detectable. By me @jsrailton.bsky.social with Rebekah Brown & @billmarczak.org citizenlab.ca/2025/06/russ...
11/ Targeting App-Specific Passwords is novel. But it's just part of a trend of state-backed attackers innovating. The folks @volexity.com have some great recent work on similar novel Russian attacks. www.volexity.com/blog/2025/04...
12/ I recommend the Google blog post on this attack. It's great that GTIG decided to post on this & go public with attribution. Helpful to victims & other research teams that don't share Google's terrifying actor visibility. By Gabby Roncone & @wxs.bsky.social cloud.google.com/blog/topics/...
13/ What next? Well if experience is a guide... I agree with Keir here. There's a good chance that whatever the attackers got will be manipulated, sprinkled with fake stuff & misleadingly framed in some future information operation. bsky.app/profile/keir...
14/ Coda: Every @citizenlab.ca report is a team production. Especially when they come together fast. Big props to my coauthors Rebekah Brown & @billmarczak.org & and the many colleagues, collaborators & coworkers that jumped in here to help out and get this report done!
15/ Plus, a special thanks to @keirgiles.bsky.social for graciously working with us to understand & get his case shared. We are all safer when people share their experiences with hacking & social engineering. They are paying it forwards.
16/ Easter Egg: I can't decide if the attackers did this MS DoS thing... - As a troll - Coincidence, didn't notice (are they zoomers?) - As a credibility enhancing thing - An LLM came up with it - ....?
📌