John Scott-Railton
@jsrailton.bsky.social
Chasing digital badness. Senior Researcher at Citizen Lab, but words here are mine.
created April 28, 2023
25,778 followers 454 following 530 posts
view profile on Bluesky Posts
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
13/ The US uses also Paragon's tech at their counterintelligence peril. Past analyses by the US highlighted how foreign spyware acquisition introduce national security & counterintelligence downsides when the company's technology is developed by foreign companies & foreign gov adjacent individuals.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
12/ Finally & unfortunately: as of right now I am pretty confident that no publicly available / commercially developed third party tool can reliably detect Paragon spyware. Beware a false sense of security.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
11/ What can you do? Go call your member of Congress. Ask them to get briefed. Ask for oversight. And on a personal level? Apple's Lockdown Mode & Android Advanced Protection both offer some serious security benefits but neither is a silver bullet..
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
10/ After 14 years of working on this topic, I tell you this with confidence: Highly invasive mercenary spyware is a power abuse machine. It's incompatible with Americans constitutional rights and freedoms. And our legal system and civil society is not prepared for the next chapter.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
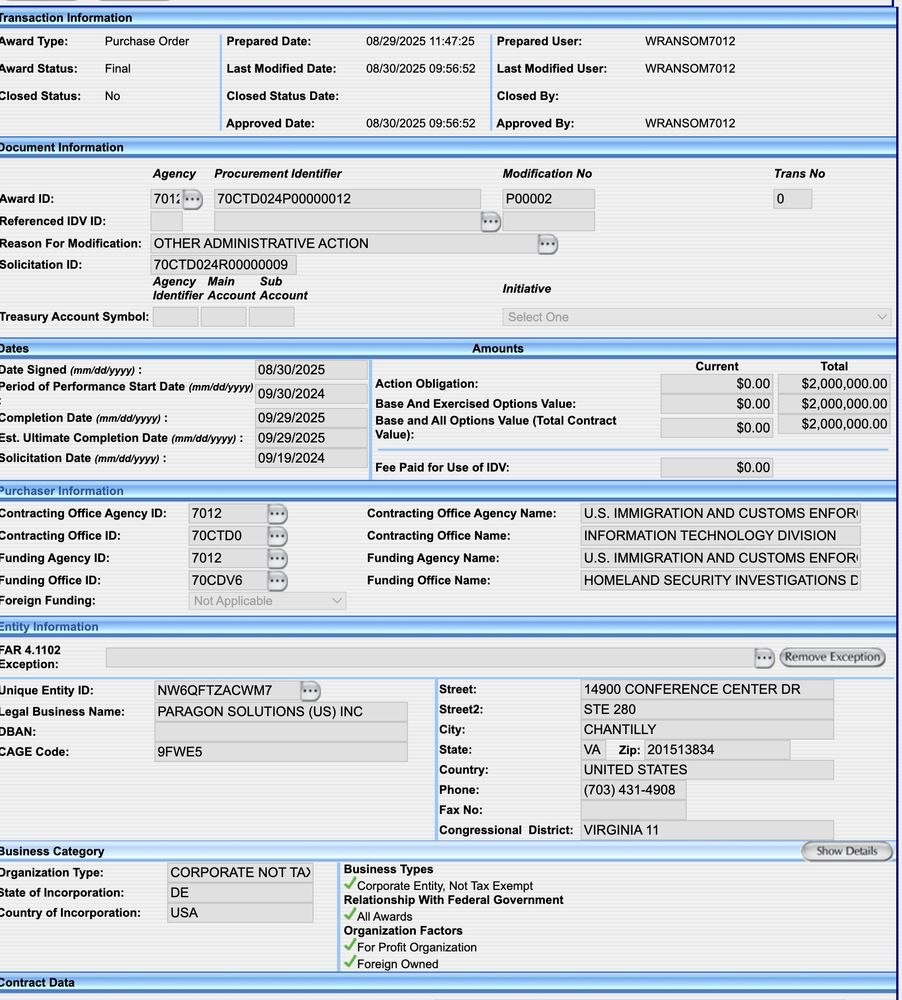
9/ Fast forwards to last weekend and the US government abruptly reopened the door for the spyware company: "This contract is for a fully configured proprietary solution including license, hardware, warranty, maintenance, and training. This modification is to lift the stop work order."
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
8/ The Italian scandal didn't finish cleanly. While the Italian authorities admitted to targeting activists, they didn't take responsibility for hacking the journalists. Meaning that some of the most troubling Paragon victims are still seeking answers.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
7/ Cases kept coming & after initial denials.. Italy had a major national scandal about surveillance overreach & spyware abuses. Ultimately the dust & a parliamentary intelligence oversight committee investigation led #Paragon & Italy parting ways... www.reuters.com/sustainabili...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
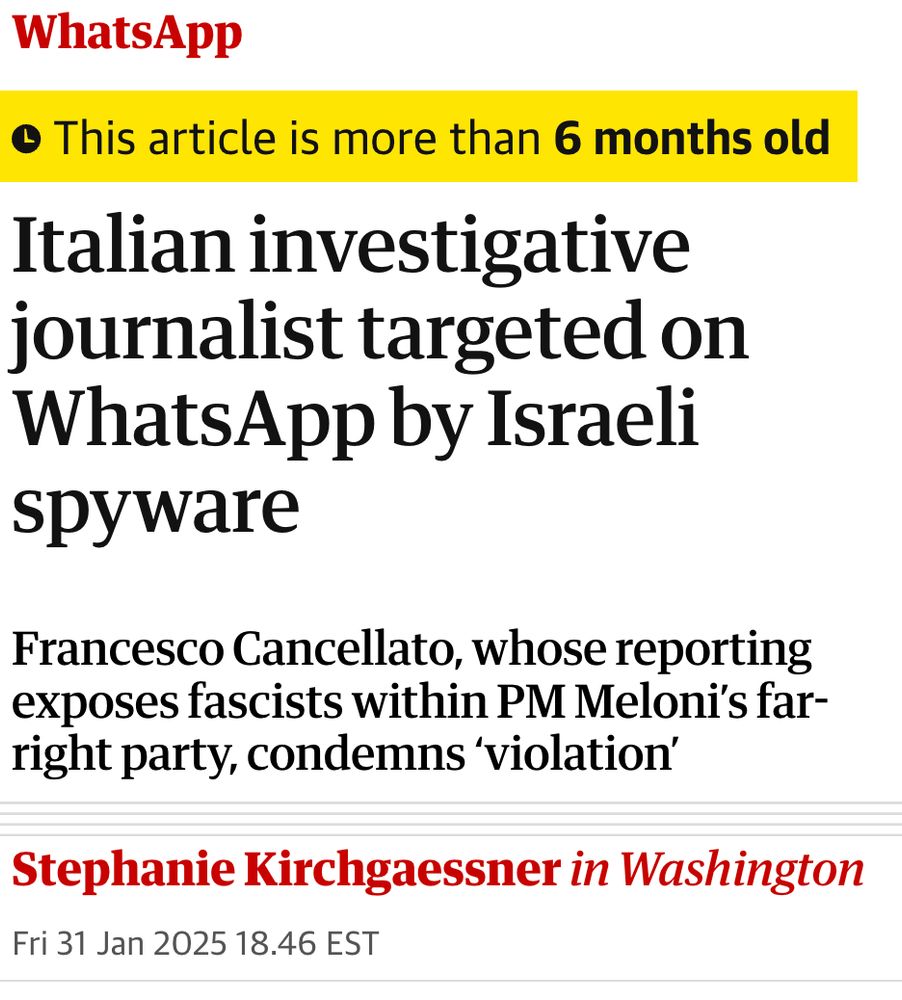
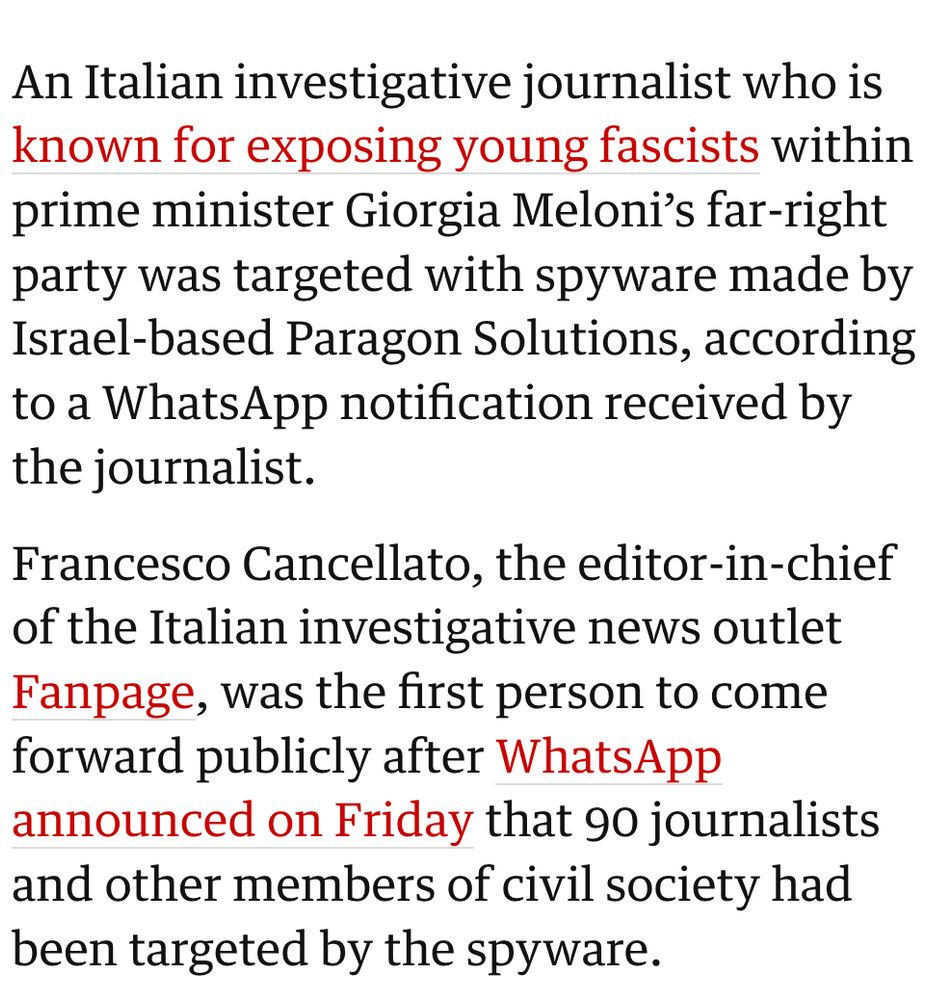
6/ Almost immediately after the WhatsApp notifications, we started learning about the targets. They weren't the supposed serious criminals... They were Journalists... human rights defenders...groups working on sea rescue of migrants.. etc By@skirchy.bsky.social www.theguardian.com/technology/2...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
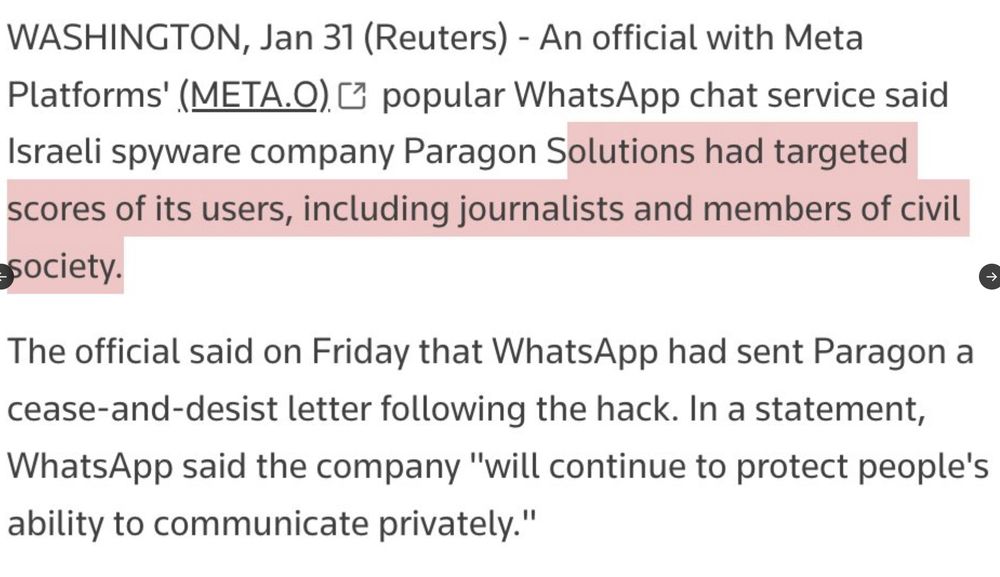
5/ Then in early 2025 #Paragon's rosy image met reality. #WhatsApp caught the company hacking people across their networks & notified targets. We worked with several & did a forensic analysis of their devices. Cases started coming out fast... By @raphae.li www.reuters.com/technology/c...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
4/ Not everything was rosy though. The White House had been on a major push to rein in spyware proliferation and somehow the ICE contract seemed to have slipped under their radar. So the contract got suspended, pending a review with the 2023 Spyware executive order.. www.wired.com/story/ice-pa...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
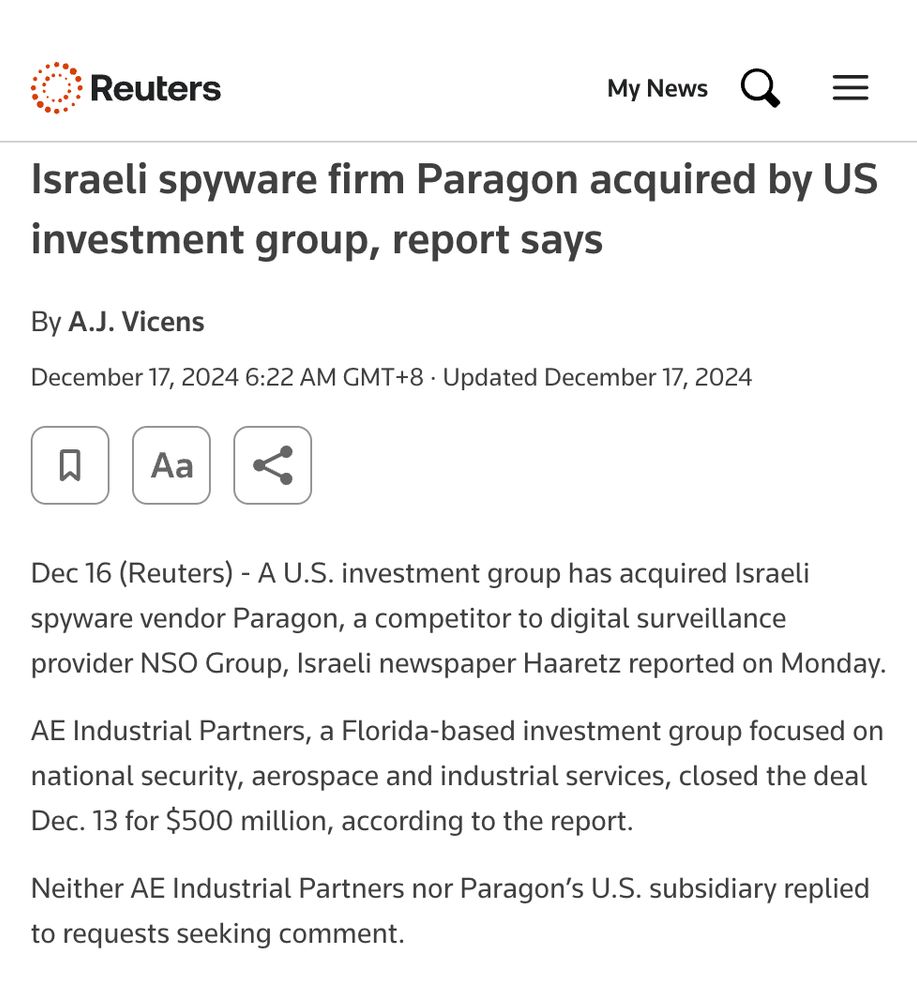
3/ Last year Paragon was flying high. They'd gotten a bunch of coverage as stealthy & they managed to get their foot in the door with a contract with ICE. Then they got. acquired by a US company. Like so many spyware companies their goal: break in to the US market. And then?
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
2/ Paragon framed themselves as the abuse-free anti-NSO. Then they had a very NSO-like spyware abuse scandal. We @citizenlab.ca caught their spyware on the phones of...journalists & human rights activists. Our investigations: citizenlab.ca/2025/03/a-fi... citizenlab.ca/2025/06/firs...
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
NEW: Mercenary spyware is coming to the US. ICE just quietly unsuspended their contract with spyware maker #Paragon. Remember them? Caught earlier this year being used to hack Italian journalists. This is bad, let's talk about how we got here 1/ jackpoulson.substack.com/p/exclusive-...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
Wait? A/B testing headlines?
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
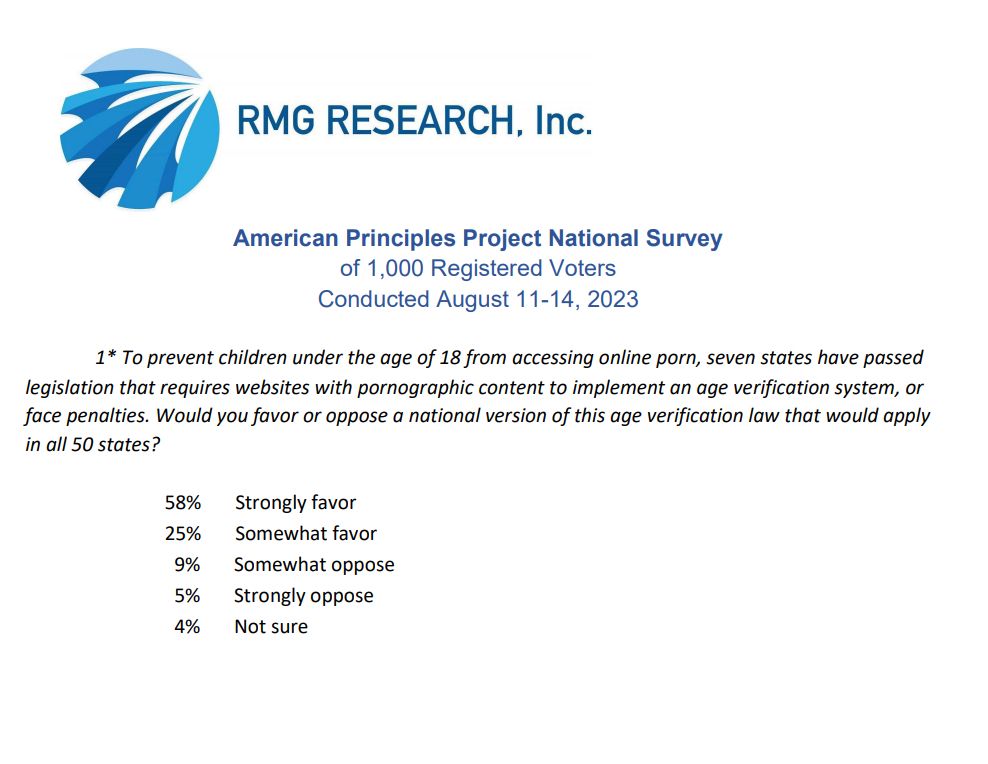
3/ Age verification laws double as a low-cost surveillance mandate. And they are coming to a jurisdiction near you. Support your local civil liberties organizations. www.eff.org/deeplinks/20...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
2/ The UK's age verification law forces law-abiding citizens to hand over personal data / scan their faces as they browse. Compelling folks to participate a massive clandestine census of browsing activity. As these troves of data grow, they expose everyone to the risk of new breaches. And worse.
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
NEW: Analysis finds UK's age verification rollout is producing exactly the opposite of the desired effect: Driving traffic non-compliant adult sites. Which punishes compliant ones. Entirely predictable. That's not the worst part 1/ By @drewharwell.com www.washingtonpost.com/technology/2...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
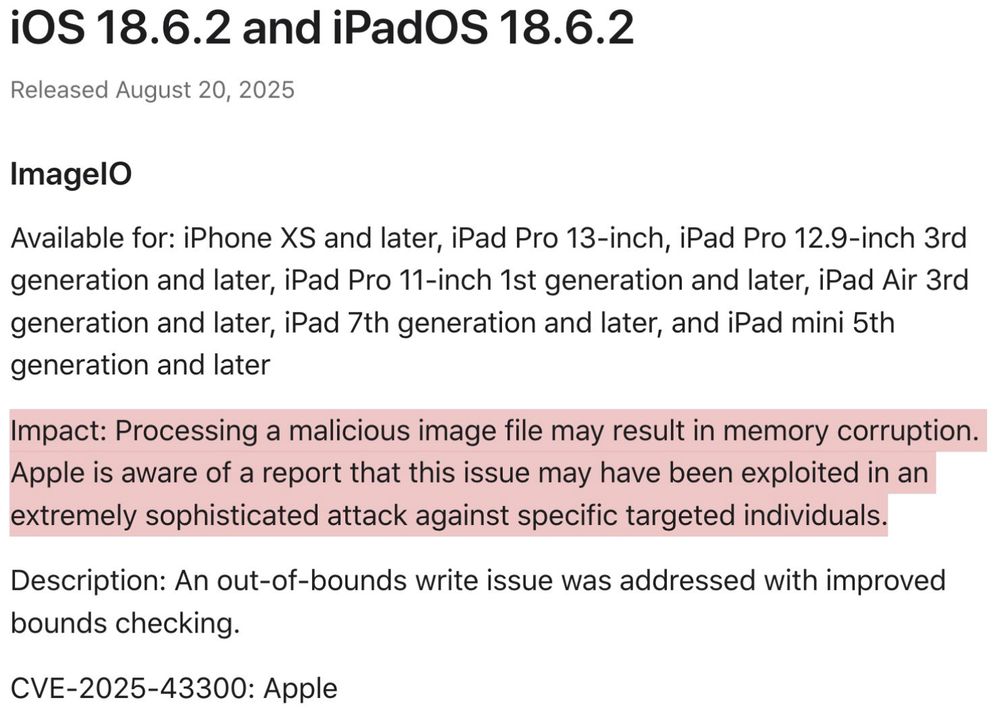
4/ Here's the Apple CVE. Somewhere, earlier this summer, some people in a room probably had a bad day when this clever cross-app chain stopped working. The cross- app chain = probably also a sign of the increasing tech lift required to get to device compromise. Consequence of various mitigations.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
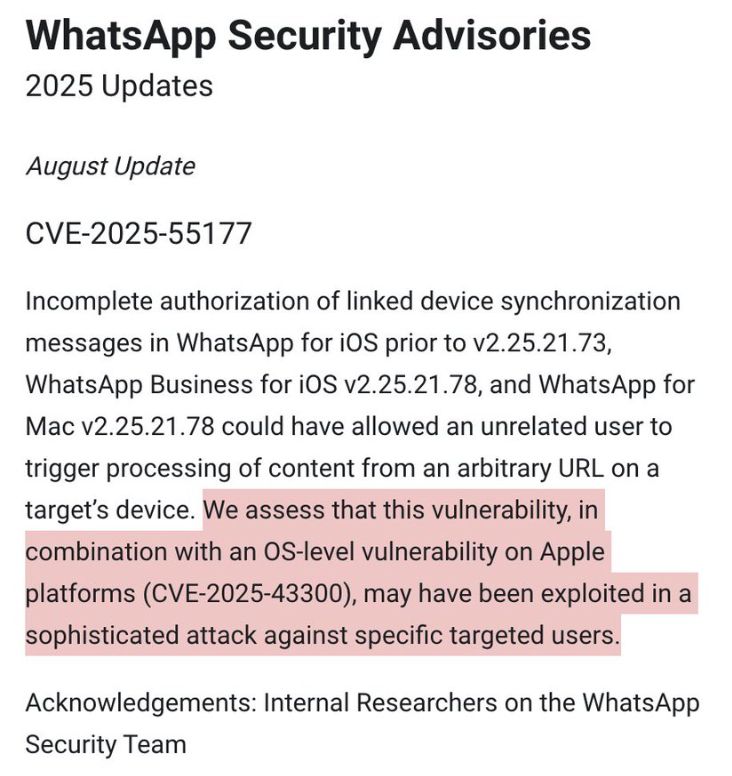
3/ The regular tempo of large platforms catching sophisticated exploits is a good sign. They're paying attention & devoting resources to a growing category: highly targeted, sophisticated attacks. But it's also a reminder of the magnitude of the threat out there... www.whatsapp.com/security/adv...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
2/ Wait, you say, haven't I heard of WhatsApp zero-click exploits not so long ago? You have. A big user base makes a platform big target for exploit development. Attacker's perspective = an exploit against a popular messenger gives you potential access to a lot of devices.
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
NEW: WhatsApp caught & fixed a sophisticated zero click attack... Now they've published an advisory about it. Say attackers combined the exploit with an Apple vulnerability to hack a specific group of targets (i.e. this wasn't pointed at everybody) Quick thoughts 1/
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
Wow. Inspiring Andy!
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
WATCH LIVE: mercenary spyware abuse is evil. But how do we bring accountability to spyware suppliers & their customers? Ft @nadinefj.bsky.social @lindsaysfreeman.bsky.social & @natynettle.bsky.social By @slpjustice.bsky.social & @cyberstatecraft.bsky.social www.youtube.com/watch?v=Hy_I...
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
Misguided age-verification laws are a universal mute button for free speech.
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
This might be the slickest free advertising the VPN industry has ever received.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
Of course, once you've 'asked nicely' for people to stop using VPNs a logical next step is implementing the Great British Firewall to start blocking them. Probably starting with demands against largest ISPs. Space to watch.
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
UK government asks everybody to stop using VPNs. "everybody who's out there thinking of using VPNs...verifying your age keeps a child safe...So let's just not try and find a way around. Just prove your age." - UK government
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
7/ Oh, and as @mozilla.org points out: only one country has banned ad-blockers. #China. Which would be terrible company for #Germany.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
6/ Here's the court case. translate with Google while you still can ;) I hope the German court seeks expert opinions from the BND, BfV and others. Perhaps they could also inquire whether these institutions already block ads to protect national security? www.bundesgerichtshof.de/SharedDocs/P...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
5/ And by the way, hacking risks from the online advertising are documented. Any attempt to force Germans to run all of the code on a website without consideration for their privacy and security rights and needs will end poorly. www.haaretz.com/israel-news/...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
4/ I'm not a lawyer but this mindblowingly misguided attempt to redefine HTML/CSS could force a radically break everything... From web search to code on GitHub to page excerpts in search results to @waybackmachine.bsky.social @archive.org and so much more... blog.mozilla.org/netpolicy/20...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
3/Defining HTML/CSS as a protected computer program will quickly lead to absurdities Potential infringements? -Screen readers for the blind -Dark mode extensions -Displaying snippets of code in a university class -Inspecting & modifying code in your own browser -Website translators On and on...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
2/Preventing ad-blocking would be a huge blow to German cybersecurity and privacy. There are critical security & privacy reasons to not blindly run all code from a site. Like stripping out dangerous code & malvertising. Or blocking unwanted trackers.
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
WHOA: megapublisher Axel Springer asks German court to ban an ad-blocker. They claim HTML/ CSS code of websites are protected computer programs. And influencing how they are displayed (e.g by removing ads) violates copyright. Endless security, privacy and technical downside & absurdity 1/
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
Logo designer deletes Lorem & calls it a day.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
Here's the thing. There are probably ALREADY datasets floating around that include the inside of the place you're in right now: - Zillow - Rental sites - AirBnB - Misc postings by you, your kids etc All of this is easy fodder for training data. All just waiting for you to post something new..
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
Post images & videos of the inside your house at your peril. This new tool uses pictures taken inside your house to identify your exact location. As a service. It will be abused to target people. For theft. Stalking. And worse.
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
X: we are actively fighting bots Also X: here's an ad for reply bots.
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
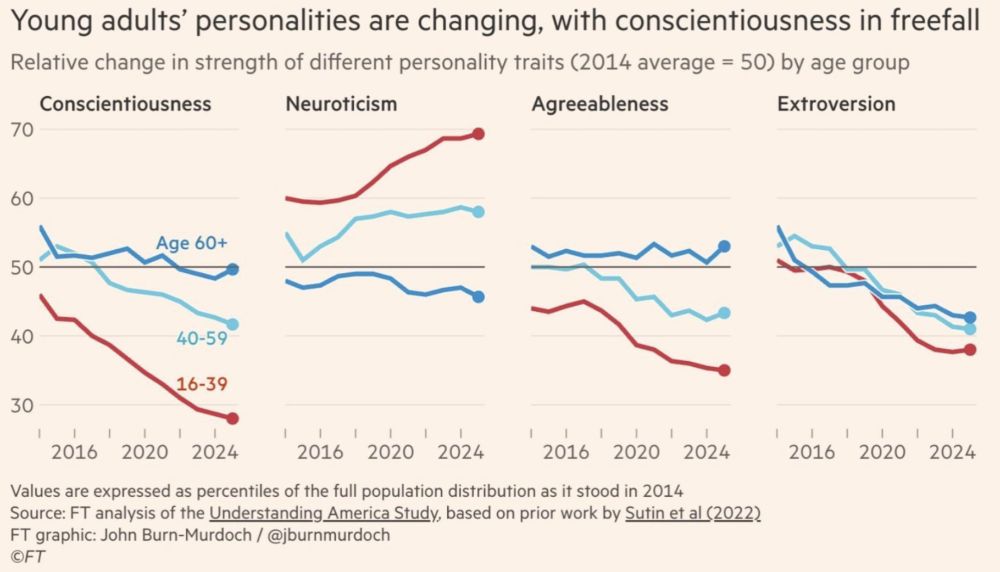
Neuroticism? Ripping. Conscientiousness & agreeableness? Dipping. Via FT: www.ft.com/content/5cd7...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
4/ In most jurisdictions, state secrecy & lack of effective legal challenges means spyware harms = happening daily Huge credit to digital freedoms organization #Digitalcourage for bringing case. Read more @therecordmedia.bsky.social by @suzannesmalley.bsky.social therecord.media/germany-spyw...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
3/ Watching Germany's highest court grapple with spyware's invasiveness & rights violations is instructive. States wielding spyware without robust legal limitations and tight judicial oversight... are almost guaranteed to be violating their citizens' basic rights.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
2/ The Federal Constitutional Court says: capturing data at the source (i.e. on someone's phone) is maximally invasive. Especially given how much of our lives happens online. They also surface the security risks to systems from this kind of surveillance.
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
NEW: 🇩🇪#Germany's top court says spyware severely violates fundamental rights. Bans spyware in cases with <3year sentences. Imposes tough proportionality tests. Restricts #spyware to serious cases. Very interesting 1/ www.bundesverfassungsgericht.de/SharedDocs/P...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
History is filled with convergent evolution...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
My prediction for the UK's Age Verification? The failure to protect children will become obvious. But the systems that force grownups to provide their IDs before sharing political views will persist. Because too many bureaucrats and certain big corporations benefit.
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
Parents know that the UK's verification rules won't really protect their kids. But they are still worried about their children's safety. They just aren't being offered non-dystopian alternatives.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
True
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
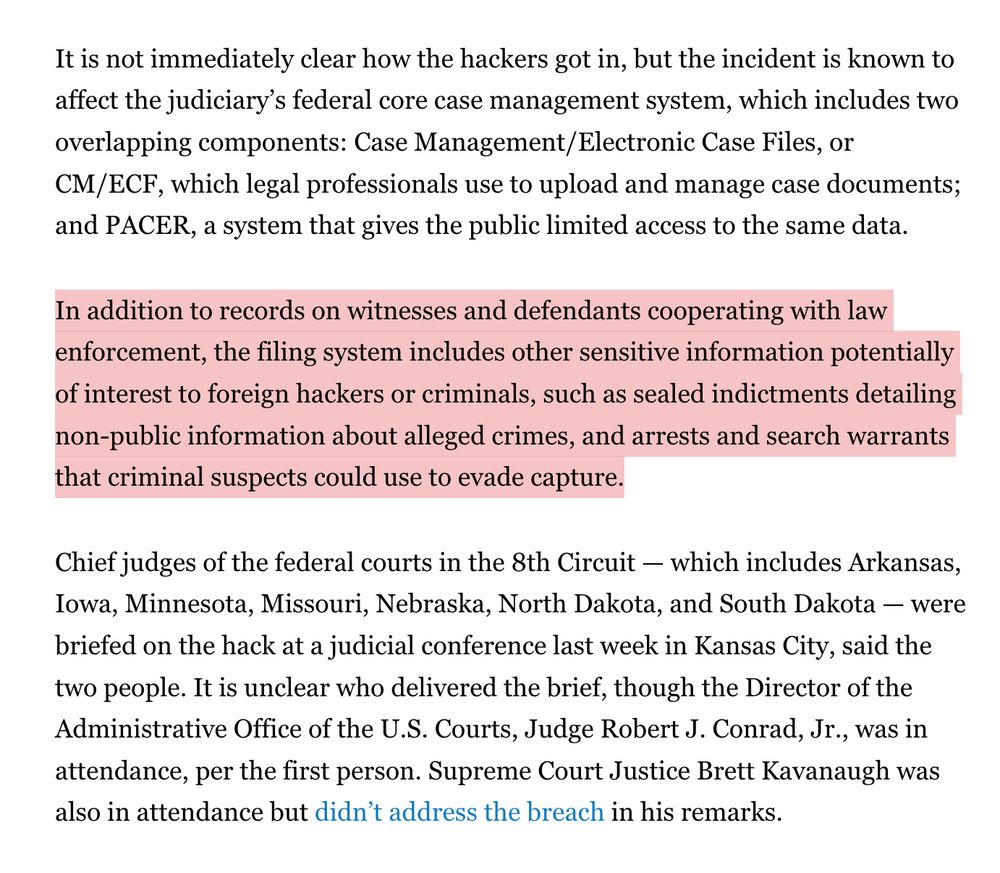
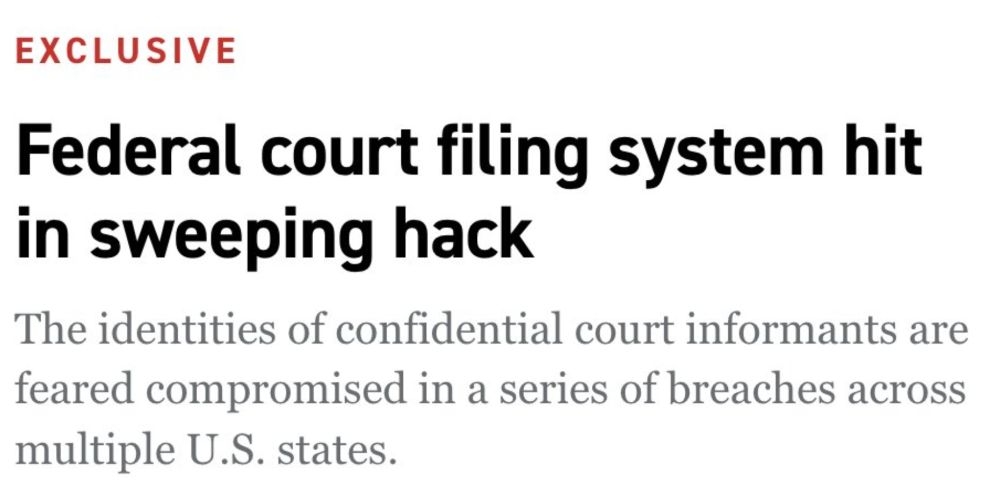
What took them so long? Maybe they had to dust off exploits from the 2000s? Or maybe the better question is: how many unnoticed breaches have happened here. It is an open secret (ask any lawyer) that these court filing systems are incredibly out of date.
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
Least shocking news ever. www.politico.com/news/2025/08...
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
What is "own goal" in Spanish? 🇨🇳China penetrated 🇺🇸American lawful intercept systems. Turbocharging espionage against the US. Puzzled wonderment that any government would bring Huawei tech into wiretapping systems.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
I hear you. The question is in the how.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
6/ We do have some models for engagement that work. I'd cite @meredithmeredith.bsky.social & related coalitions scoring big wins around chat privacy. Perhaps folks can point me to others? But ultimately we need so much more of this kind of high-impact engagement in front of big public audiences.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
5/ Personally? Maybe we need to talk about empowering parents, not bureaucrats with hidden agendas. Or supporting healthy communities, not corporations. Ultimately, we need to stand up for the next generation. And their autonomy.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
4/ Am I missing high-impact framing happening somewhere on age verification? I've been hunting for things like: 1- Reframing around values like parental autonomy 2- Highlighting risks to children from profiling (kids not suspects!) 3- Powerful harm anecdotes 4-Offer parental tools & alternatives.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
3/ Seems like there are some big gaps in the age verification fight: - Widespread framing that makes *enough sense* to the vast majority of people that they say 'ok this is net bad' - Productively connecting with same anxieties politicians are drawing on - Offering alternate paths & futures
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
2/ Saying that something speeds us towards surveillance dystopia works on me. But not my neighbors. Sure, most here intuitively understand the dangers... And nod along when we gesture at the dangers of surveillance overreach. But for the general public, I'm not sure how well this works.
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
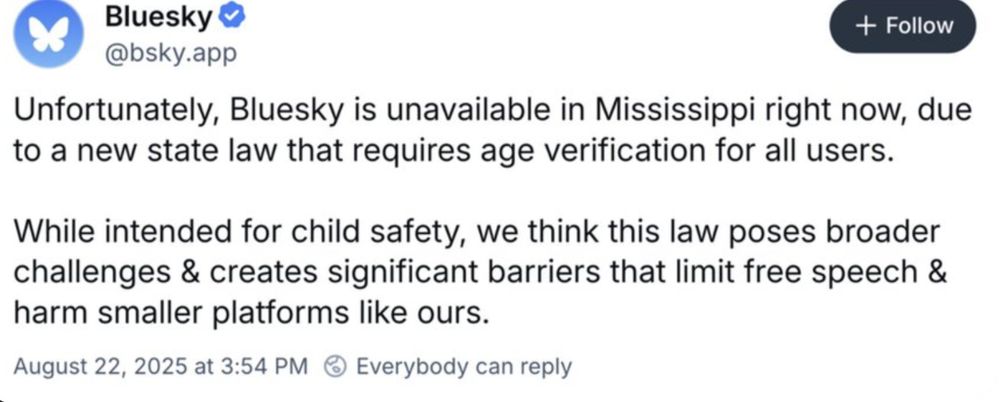
Age verification laws are coming fast. And, from my perspective, opponents are struggling to find impactful messaging for the general public to frame damage they are about to do to freedom. Or to propose alternate futures that address the underlying anxieties. 1/
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
It seems to me like a strong anti-AI stance is becoming left-coded. I'm hoping to disentangle criticisms of biz models, power-grabs, externalities (e.g. labor disruption, environmental impact), privacy etc.. vs. views on AI itself, especially when used in open-source ways. Thoughts?
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
Rhinoisotope
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
7/ And when the strong leader dies? The society can be incredibly unstable as it carries the weight of so many injustices, so many lies. And for the system to persist? More repression needed.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
6/ Because self-censorship scales better than physical coercion on each person. People see opportunity for personal advantage. Some become informers. Some delight in the cruelty of seeing people they dislike arbitrarily punished.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
5/ People with new, better ideas that also happen to challenge the dictators entrenched interests? Or those of the dictators necessary economic allies? Family members? Point out corruption? Co-opted or cut down. Fueled by massive surveillance. And the threat of violence.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
4/ People with ambition need to play into the system and help prop up the dictator if they want to keep their resources. Even then they are vulnerable to having everything taken. And for anyone that dares point out increasingly obvious flaws? Well, dictatorships will slide into repression.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
3/ Care about equality of opportunity? dictatorships concentrate power without balance. Over time as inequalities & unfairness become severe... the rule gets more brittle. And dictators have to give more favors to the people that help them stay in power. Like economic favors.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
2/Even when dictatorships do 'well' on a factor, in the short term, they send people into a freedom-robbing labyrinth. In the long run with dictatorships you lose out on the chance for a society that supports freedom, personal rights & liberties & decentralization of knowledge + innovation.
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
It is a lot easier to celebrate a turn towards dictatorship when you are untethered to historical knowledge. No amount of centralized power delivers a society with true personal freedom in the long run. 1/
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
What's something that teenage you thought was peak.. But adult you sees as weak? I'll go first: MENSA.
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
Consider, your Honor, that my client was being extremely productive at the time of the crash.
 Ron Deibert (@rondeibert.bsky.social) reposted
Ron Deibert (@rondeibert.bsky.social) reposted
Couple of weeks ago we @citizenlab.ca published a report on a sophisticated Russia-linked 🇷🇺 phishing campaign targeting a UK-based Russian critic and analyst citizenlab.ca/2025/06/russ... The target @keirgiles.bsky.social has written an excellent overview: foreignpolicy.com/2025/07/02/g...
 Luis Fernando García (@luisfgarcia.bsky.social) reposted
Luis Fernando García (@luisfgarcia.bsky.social) reposted
In Mexico 🇲🇽, Sheinbaum's government is pushing through Congress sweeping legal reforms that will establish mass identification and surveillance systems of the population. Here is a thread 🧵 summarizing the scope and reach of these reforms:
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
This is a tool for one person to acquire a lot of power. Sam Altman wants his technology to become unavoidable, and mandatory. He makes the problem. Then we depend on him to fix it. Bad move for privacy & freedom. Worse move for #Reddit , which he might very well one day compete against.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
This is an interesting idea & has been experimented with by some cool artists & projects (also me, more informally) But it only works on certain kinds of optical facial recognition that depend on infrared illuminators. FR that does visual spectrum stuff is not bothered by this.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
That's cool! And it's the right thing to make exceptions for use cases that help people with accessibility. That said, I am comfortable criticizing products designed & overwhelmingly used for corporate surveillance. And to discourage their proliferation.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
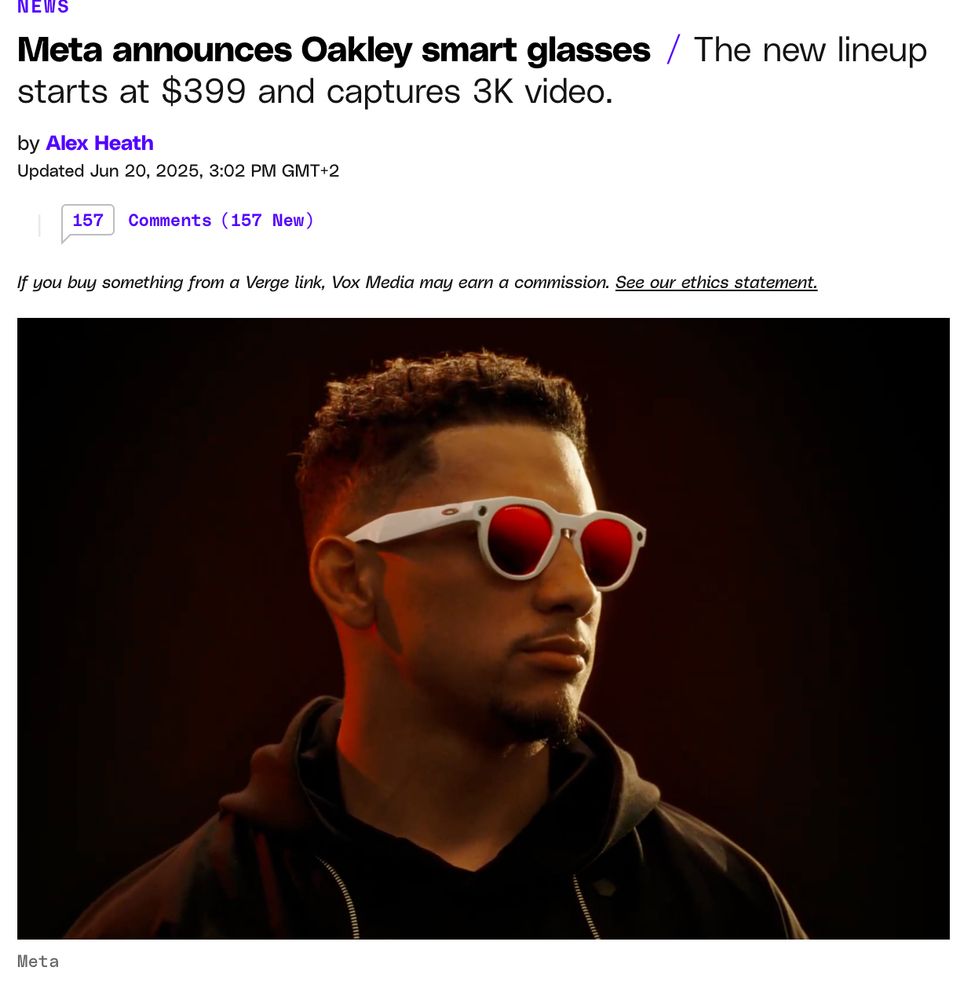
Computer vision & HUDs are cool. AI augmented reality is fascinating. But this is a trojan horse for megacorp to get into *all* your interactions. Friends don't let friends bring Zuck in a backpack on their adventures.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
Or, wear these Dorkleys yourself & become an NPC constantly asking your eyewear 'hey meta is this real?'
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
I prefer the company of people that don't snitch my business.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
Sometimes I think that the big phishing operations have probably developed a more applicable & empirically tested understanding of human motivation and cognition than psychologists... Tens of thousands of behavioral A/B tests a day...and that would be a low number.
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
You can patch software, but you can't patch people. Social engineering will always work because human brain is loaded with forever-day vulnerabilities...
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
UPDATE: Looks to me like Paragon is again feeling the heat, and tossing the Italian government under the bus. The scandal continues.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
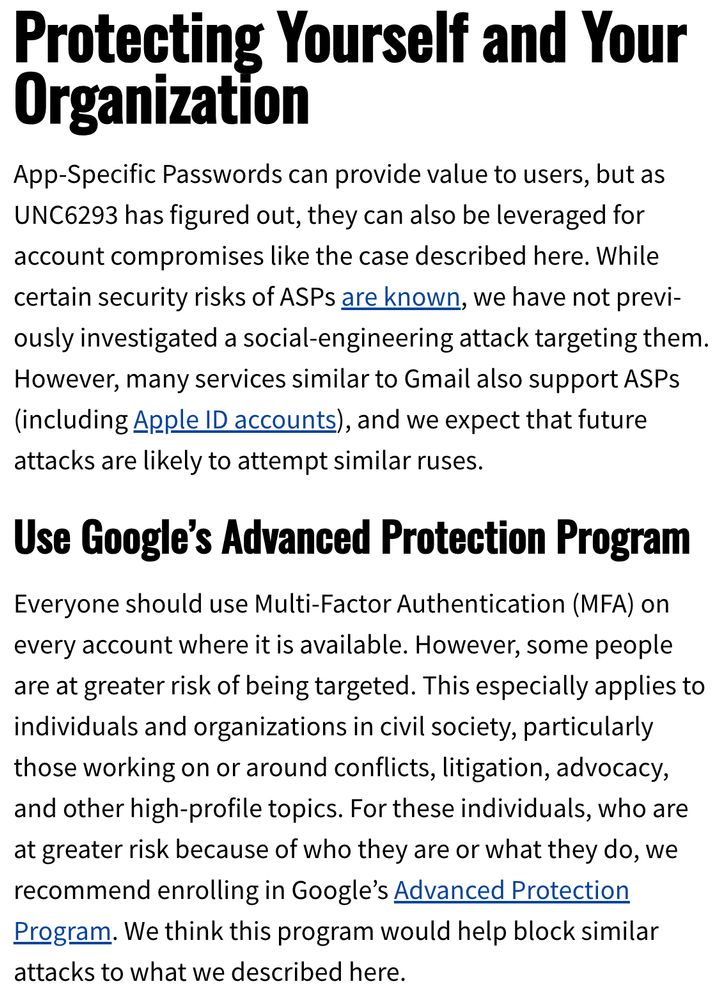
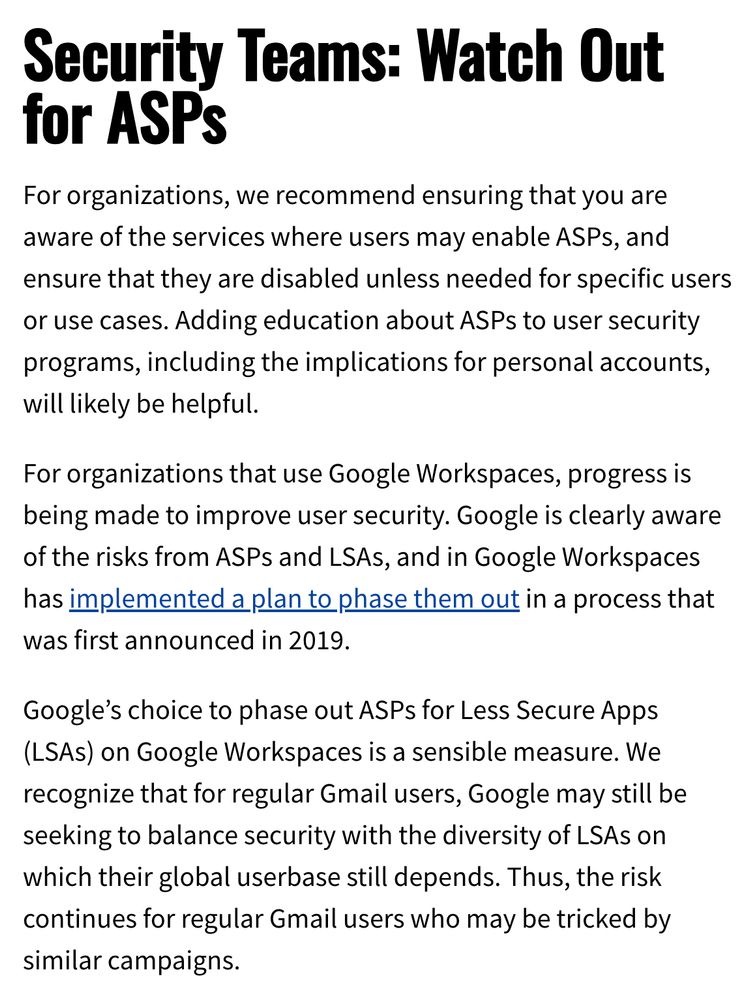
17/ Do you think you face increased risk because of who you are & what you do? Use Google's free Advanced Protection Program. SET IT UP NOW: landing.google.com/intl/en_in/a... And exercise extra skepticism when unsolicited interactions slide into suggesting you change account settings!
 Raphael Satter (@raphae.li) reposted
Raphael Satter (@raphae.li) reposted
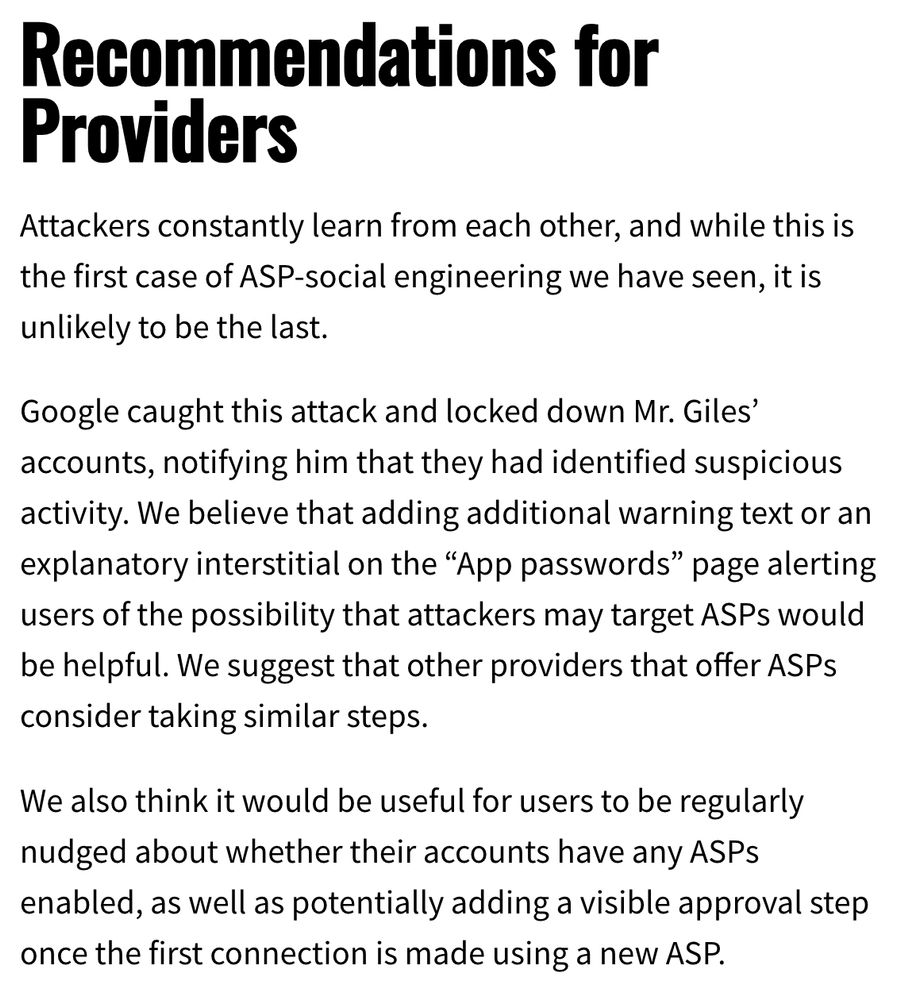
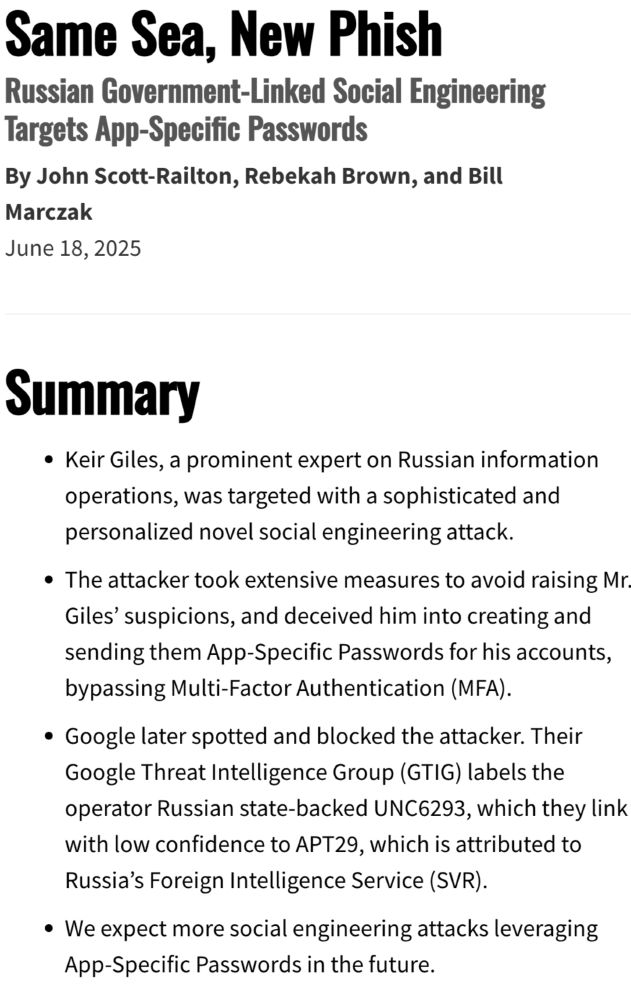
Keir Giles has been targeted *again* by allegedly Russian hackers — this time using a clever new trick intended to bypass 2-factor authentication. Over the years I’ve written about Giles an unusual amount, and I have an idea about why. First, the coverage: www.reuters.com/technology/s...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
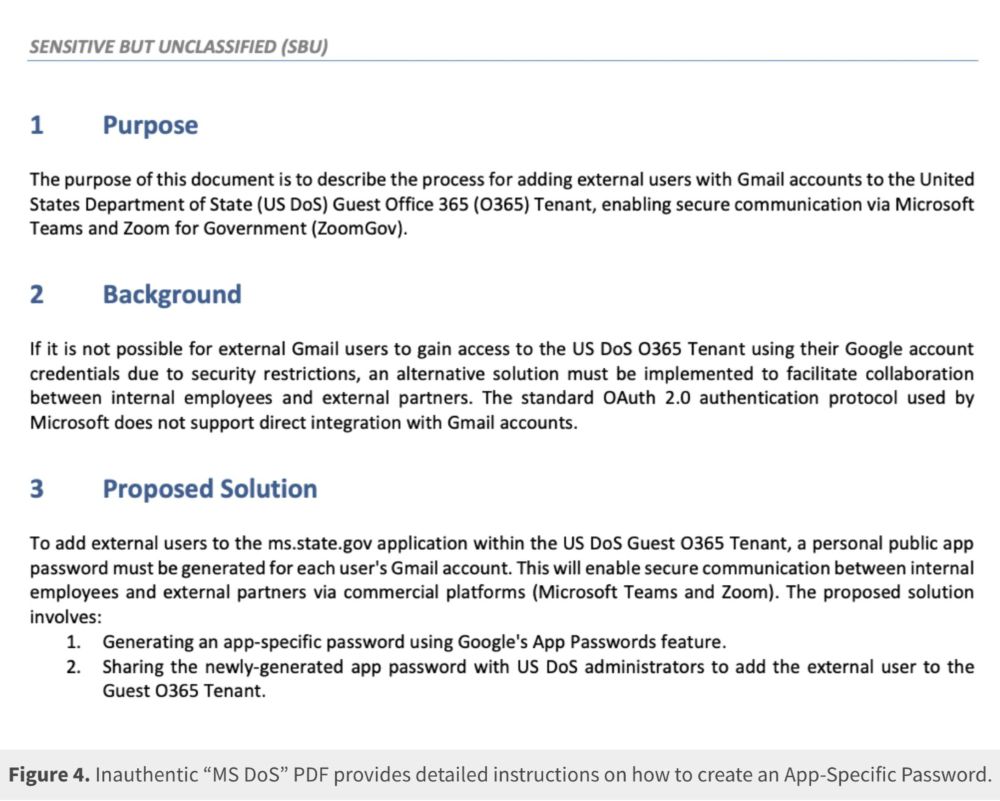
16/ Easter Egg: I can't decide if the attackers did this MS DoS thing... - As a troll - Coincidence, didn't notice (are they zoomers?) - As a credibility enhancing thing - An LLM came up with it - ....?
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
you bet it does!
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
15/ Plus, a special thanks to @keirgiles.bsky.social for graciously working with us to understand & get his case shared. We are all safer when people share their experiences with hacking & social engineering. They are paying it forwards.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
14/ Coda: Every @citizenlab.ca report is a team production. Especially when they come together fast. Big props to my coauthors Rebekah Brown & @billmarczak.org & and the many colleagues, collaborators & coworkers that jumped in here to help out and get this report done!
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
13/ What next? Well if experience is a guide... I agree with Keir here. There's a good chance that whatever the attackers got will be manipulated, sprinkled with fake stuff & misleadingly framed in some future information operation. bsky.app/profile/keir...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
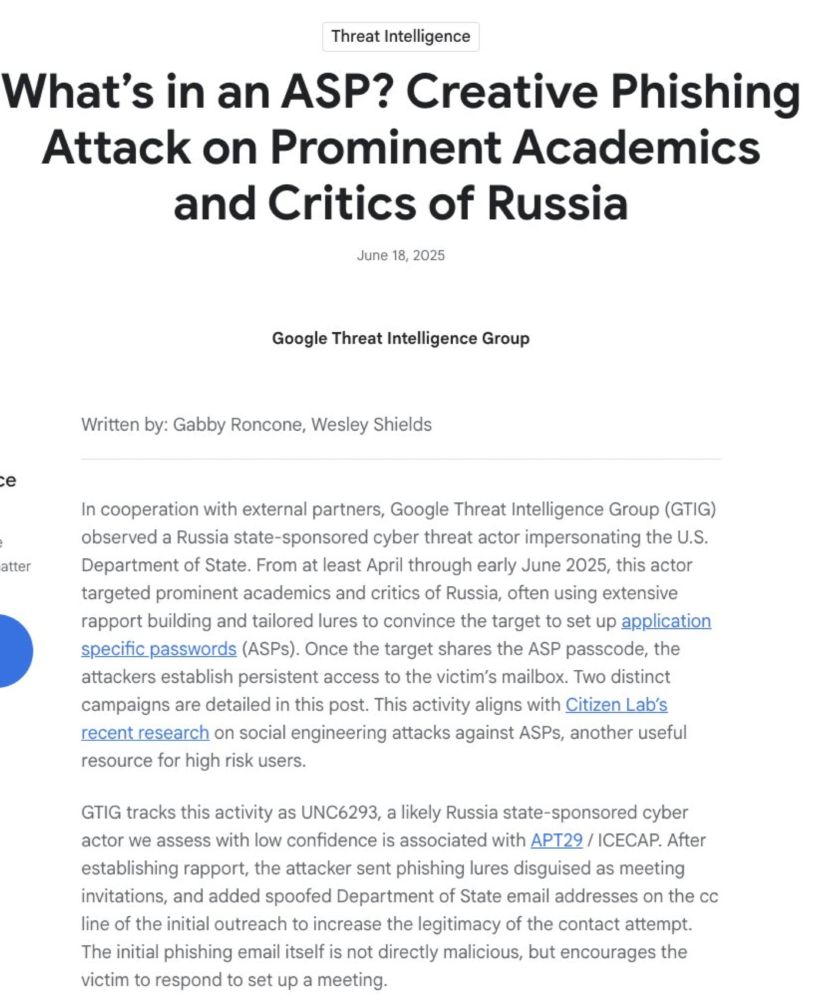
12/ I recommend the Google blog post on this attack. It's great that GTIG decided to post on this & go public with attribution. Helpful to victims & other research teams that don't share Google's terrifying actor visibility. By Gabby Roncone & @wxs.bsky.social cloud.google.com/blog/topics/...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
My theory is that it's about trying to prevent enumeration.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
11/ Targeting App-Specific Passwords is novel. But it's just part of a trend of state-backed attackers innovating. The folks @volexity.com have some great recent work on similar novel Russian attacks. www.volexity.com/blog/2025/04...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
10/ Takeaway: some gov-backed groups are feeling pressure & experimenting. Moving from smash & grab phishing... to subtler, slower & perhaps less detectable. By me @jsrailton.bsky.social with Rebekah Brown & @billmarczak.org citizenlab.ca/2025/06/russ...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
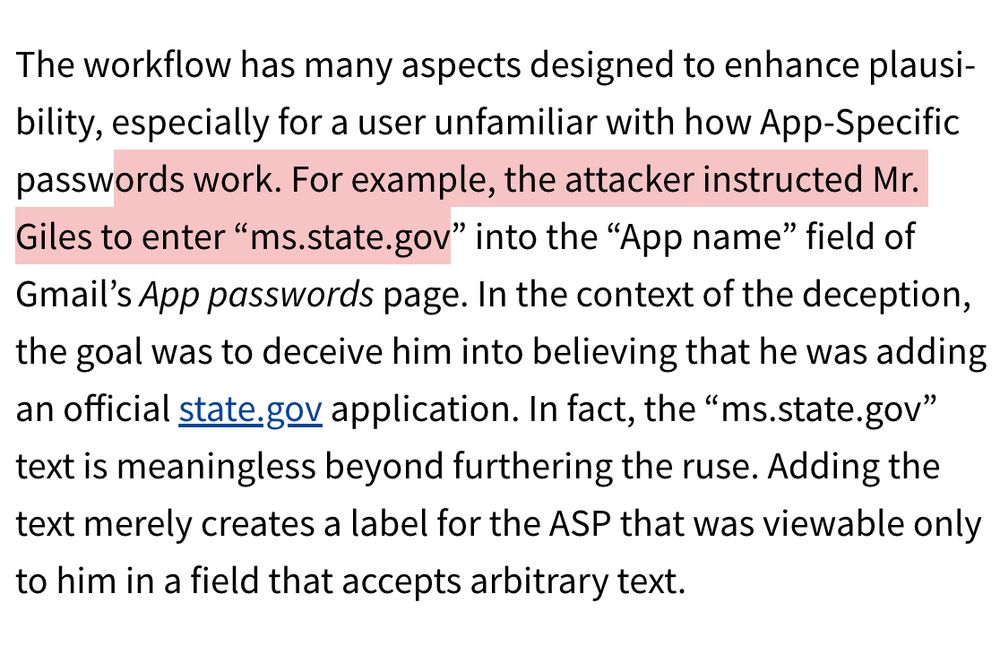
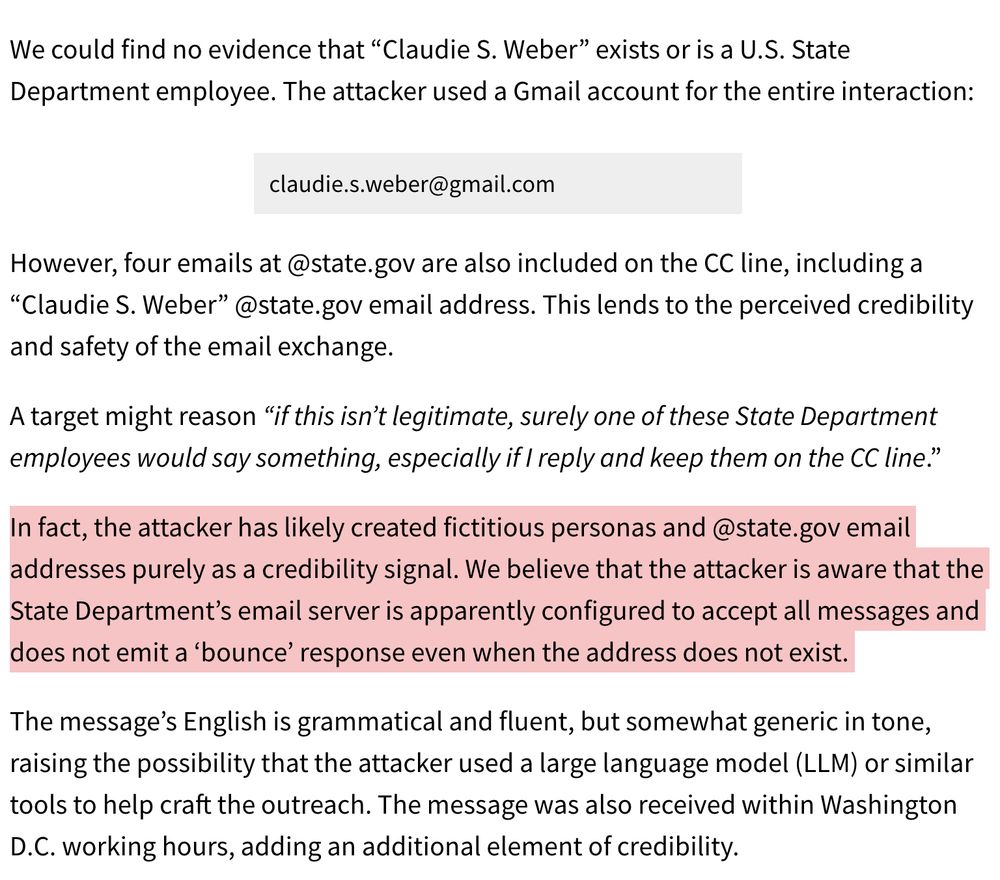
9/ There were so many clever bits to this attack, it's easy to imagine a lot of people falling for it. Everything was clean. Foc looked real. The language was right. Email addresses at the State Dept. seemed to be CC'd.. I could go on. They even had Keir enter "ms.state. gov" into the ASP name...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
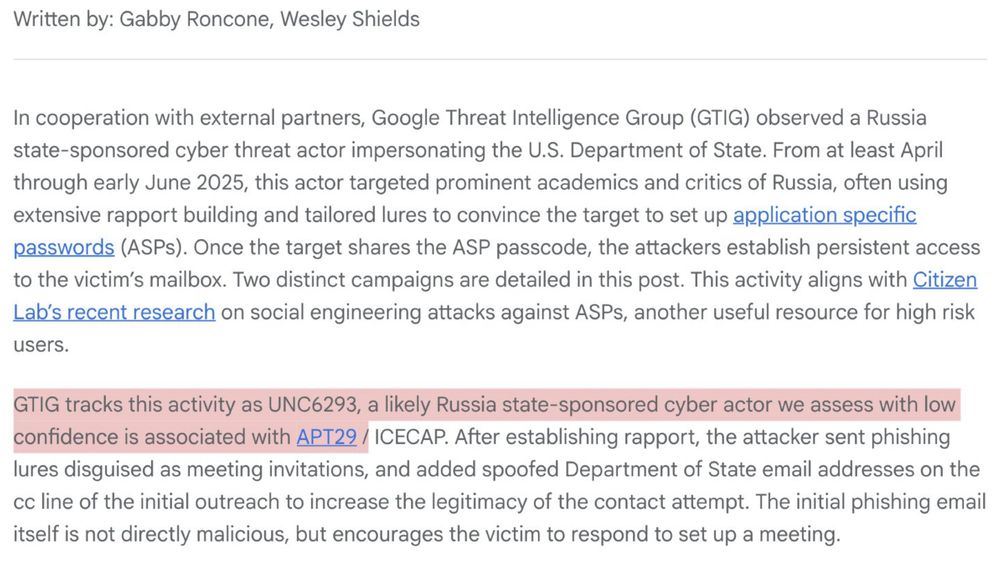
8/ Who targeted @keirgiles.bsky.social ? Enter the Google Threat Intelligence Group w/analysis & attribution! Great! Our bad actors are: 🇷🇺 #UNC6293, a #Russian state-sponsored threat actor. Google adds bonus additional low confidence association to #APT29 (that would be the #SVR). Nice people.
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
7/ This attack was like slow food. 10 email exchanges over several weeks! No overt pressure! Very much not your run-of-the-mill phishing. Ultimately, @keirgiles.bsky.social realized something was wrong and got in touch with us @citizenlab.ca...but not before the attackers got some of his ASPs...
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
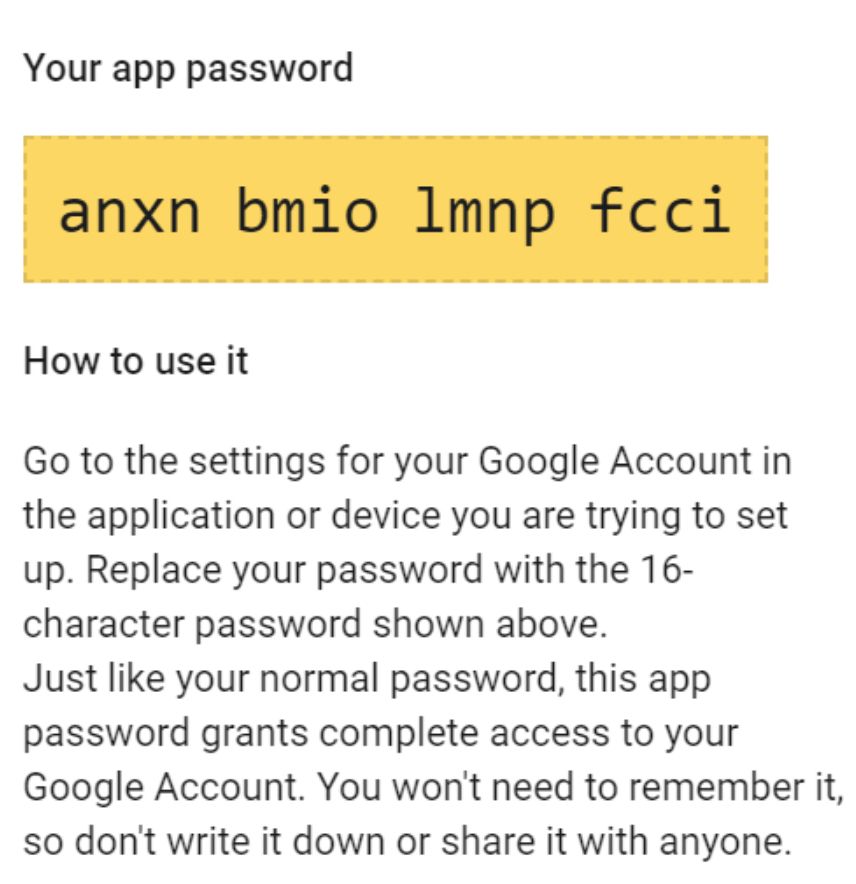
6/ What's an App-Specific Password? So, not every app supports Multi-Factor Authentication. Some older email clients don't. So providers like Google let users create a special password just for those apps. An ASP is a string of characters that give access to *everything* See where this is going?
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
5/ The attack works like this: deceive @keirgiles.bsky.social into creating & sending the attacker an App-Specific Password (ASP). They do this by reframing ASPs as something that will let him access a secure resource (spoiler: not how this works).. So, what IS an ASP for real tho?
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
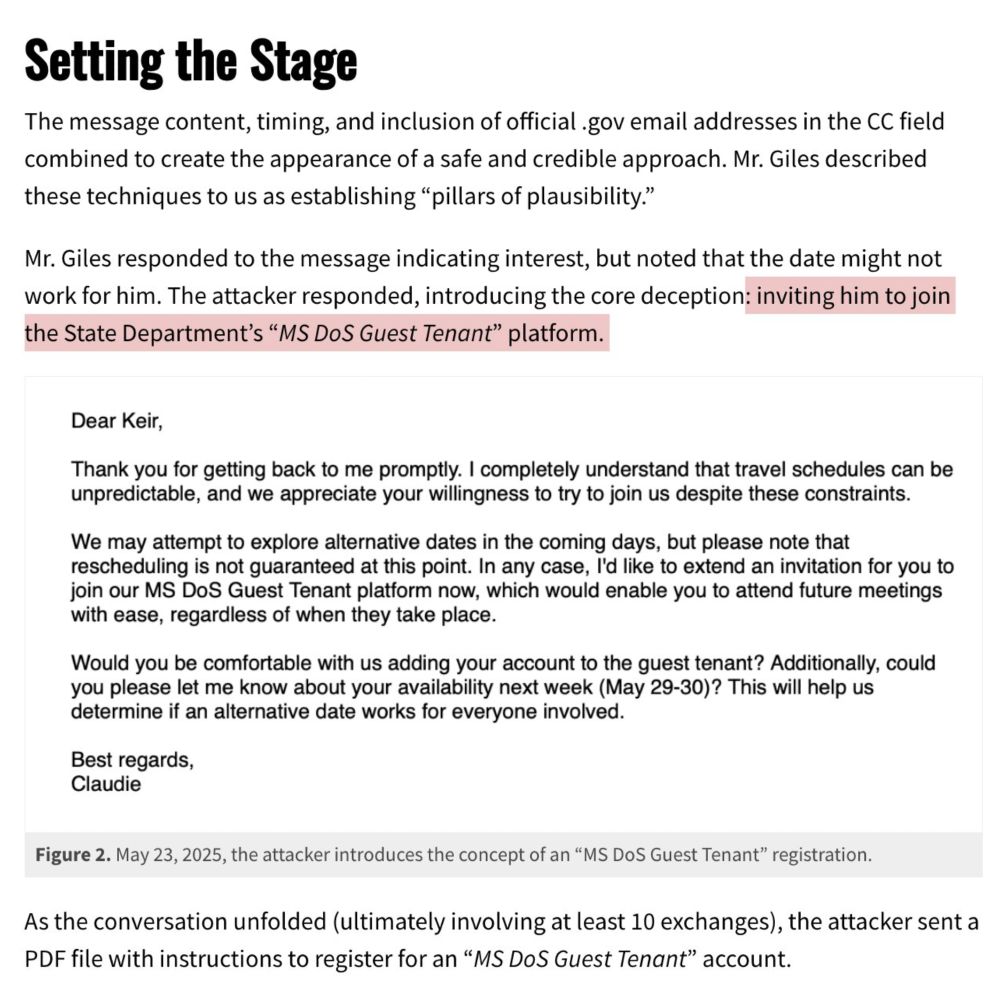
3/ The attackers wait for the 2nd interaction to introduce the pivotal deception: getting @keirgiles.bsky.social to 'connect to a secure platform. In the next days they patiently walk him through what they want him to do, even sending a very official looking (but fake) State Dept. document
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
3/ Strong credibility signal to have a bunch of .gov ppl on a CC line right? Well, the #Russian attackers must've figured out that the State Dept mailserver just accepts all email to ANY @state.gov address without a bounce. So they just added some fake State Dept staff names and addresses. Smart!
 John Scott-Railton (@jsrailton.bsky.social) reply parent
John Scott-Railton (@jsrailton.bsky.social) reply parent
2/ How the attack works: First. @keirgiles.bsky.social gets a message purporting to be from the State Dept asking for a consultation. Pretty common thing for him. And these attackers did everything to make this outreach look credible... Like CCing a bunch of @state.gov email addresses...
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
🚨NEW REPORT: exposing clever new hacking tactic. 🇷🇺Russian state-backed hackers used an App-Specific Password attack against prominent Russia expert @keirgiles.bsky.social It's like they knew what we all expect from 🇷🇺...and then did the opposite 1/ By us @citizenlab.ca & Google's GTIG
 John Scott-Railton (@jsrailton.bsky.social)
John Scott-Railton (@jsrailton.bsky.social)
🇨🇦Canada speaking out about the proliferation of mercenary spyware. It's a start after a puzzlingly long silence. My colleague @citizenlab.ca director Ron Deibert has a good thread.👇
John Scott-Railton (@jsrailton.bsky.social) reply parent